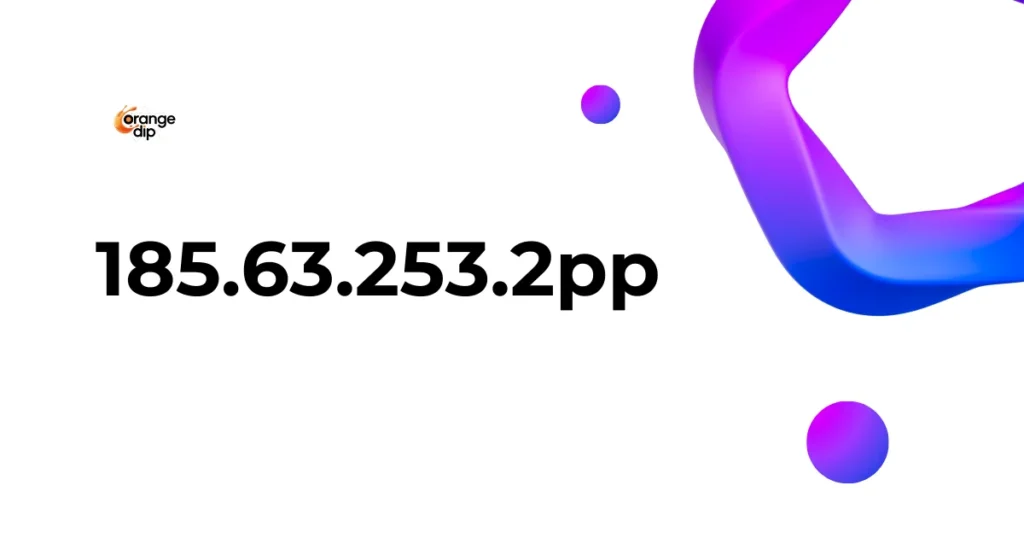
When strange entries like 185.63.253.2pp show up in server logs or analytics, it often raises questions. At first glance, it looks like a regular IP address, but the extra “pp” makes it unusual and confusing. Many users wonder if it signals a security risk, bot traffic, or simply a logging error.
Since online threats often hide behind suspicious-looking data, understanding what 185.63.253.2pp means is important. This guide explains the possible origins, risks, and ways to investigate, giving you clarity and practical steps to protect your systems while avoiding unnecessary panic.
What is 185.63.253.2pp
The entry 185.63.253.2pp looks like a standard IPv4 address, but technically it is not. The numeric part, 185.63.253.2, is valid, while the “pp” suffix is unusual and not part of normal IP formatting.
In many cases, this label appears in logs, proxy connections, or analytics spam. Some interpret “pp” as a shorthand for proxy, port, or private protocol. Although it isn’t officially recognized, its presence signals unusual activity worth checking.
Also read, What Are the Best Ways to Get PG Soft Medals on Juara100.org
Who Owns 185.63.253.2
A quick WHOIS lookup shows that the IP 185.63.253.2 is linked to a hosting provider called HostPalace Datacenter. The servers are based in Amsterdam, Netherlands, which often hosts proxy and VPN services.
While the ownership itself is legitimate, traffic from this address can include bots, automated crawlers, or spam activity. This makes it important to separate harmless use from suspicious behavior. Checking the IP reputation databases helps confirm whether 185.63.253.2pp poses a real risk.
Why 185.63.253.2pp Appears in Logs

The entry 185.63.253.2pp often shows up in server logs or analytics reports when unusual traffic reaches your site. It may come from proxy servers, VPN users, or automated bots scanning the web. Sometimes, it appears as referrer spam in Google Analytics, creating confusion and fake sessions.
In other cases, it can be linked to security probes testing site vulnerabilities. Understanding these patterns helps identify whether the IP activity is harmless background traffic or a potential risk.
How to Investigate 185.63.253.2pp
| Tool | Purpose | Benefit |
|---|---|---|
| WHOIS Lookup | Checks IP ownership & location | Identifies datacenter/host |
| AbuseIPDB | Reviews abuse history | Detects spam or attacks |
| VirusTotal | Scans reputation across databases | Confirms malicious activity |
| Reverse DNS | Finds associated domains | Links IP to services |
| Log Analysis | Reviews traffic behavior | Spot bots & unusual patterns |
Investigating 185.63.253.2pp starts with a WHOIS search to check domain ownership and network details. Next, use tools like AbuseIPDB or VirusTotal to see if the IP has a history of abuse.
A reverse DNS lookup can reveal its host, while checking server logs, user agents, and request patterns helps detect bots. You can also review the ASN and netblock to understand the source. These steps separate harmless visits from suspicious or malicious traffic.
Security Risks of 185.63.253.2pp
Traffic from 185.63.253.2pp can pose several security risks. It may be linked to bot activity, brute-force login attempts, or web scraping that overloads servers. In some cases, it appears as referrer spam in analytics, distorting real data.
Hackers may also use such IPs to hide behind VPNs or proxy networks while probing for vulnerabilities. Although not every hit from this address is harmful, ignoring unusual traffic patterns can expose your site to potential attacks.
Also read, G15Tools.com Contact Guide: Email Support & Feedback Made Easy
How to Block or Filter 185.63.253.2pp
| Method | Platform | Example Use |
|---|---|---|
| Firewall Rules | iptables, nginx, Apache | Block IP manually |
| Cloudflare Filter | Cloudflare dashboard | Simple block rule |
| Google Analytics Regex | GA filter settings | Exclude spam traffic |
| Security Plugins | WordPress/Drupal | Auto-block suspicious IPs |
If 185.63.253.2pp causes unwanted traffic, you can block it using firewall rules in iptables, nginx, or Apache. For websites, platforms like Cloudflare make it easy to filter suspicious IPs. In Google Analytics, regex filters can exclude spam visits and keep data clean.
WordPress users can rely on security plugins to block harmful requests. Regularly updating your filters and monitoring activity ensures better protection, preventing bots and proxy traffic from disrupting site performance.
False Positives and When Not to Block
Not all traffic from 185.63.253.2pp is harmful, so blocking it blindly can cause false positives. Some visits may come from legitimate VPN users, crawlers, or testing services. Before adding a block rule, always review logs, traffic patterns, and reputation checks.
If the IP shows normal browsing behavior without suspicious requests, it may be safe to leave it. Over-blocking can cut off real visitors, so a balanced approach protects security without harming user access.
Preventing Future Unknown IP Issues
Dealing with strange entries like 185.63.253.2pp becomes easier when you set up proactive defenses. Enable firewall alerts to detect suspicious IPs in real time. Use automated scripts or security tools that check IP reputation databases regularly.
Keep server logs organized and review patterns for abnormal activity. Adding WAF protection and rate-limiting helps stop bots before they overload your site. Preventing unknown IP issues early saves time, protects your analytics, and strengthens overall online security.
FAQs
Is 185.63.253.2pp a real IP?
No, the base IP is valid, but the “pp” suffix is unusual.
Can it harm my site?
It may link to bots, spam, or proxy traffic.
How do I check it?
Use tools like WHOIS, VirusTotal, and AbuseIPDB.
Should I block it?
Only if it shows suspicious behavior in logs.
Does it affect SEO?
Referrer spam can distort analytics but won’t harm rankings directly.
Conclusion
The unusual entry 185.63.253.2pp often raises concern, but understanding its meaning, risks, and investigation steps makes it less confusing. While some cases involve harmless proxy or VPN traffic, others may point to bots or spam activity.
The key is to verify before blocking, use WHOIS lookups, and rely on IP reputation checks. With proper monitoring, firewall rules, and filters, you can manage such anomalies effectively, keeping your website security strong without disrupting real visitors.